protecting computer malware nashville virus cleanup
Protecting your computer from malware and dealing with an infected computer can be one of the most frustrating problems that computer users face. Not only can malware(viruses) keep your computer from running properly, it can also jeopardize the security of your personal information. As a result, it is important for computer users to know how their computers can get infected in the first place, as well as how to prevent any malware from infecting their computers.
Click After Reading
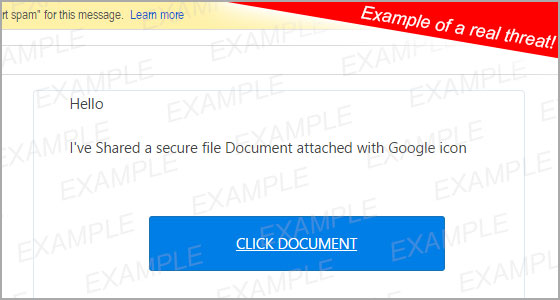
One of the most common ways that a computer can become infected is when a computer user accepts a message that appears on their screen before they even read what it says. For example:
- An Internet advertisement or window pops up and tells you that your computer requires a specific plug-in or that your computer is already infected with malware. By downloading the plug-in or accepting the message without fully understanding what is happening, you may have unknowingly subjected your computer to infection.
- When updating or installing a computer program, you may be prompted to install additional programs that you do not need or that could monitor your use of the original program. These additional programs could cause significant problems for your computer and could even subject it to infection.
Downloading Infected Software
Another common way that a computer can become infected is when a computer user downloads software programs from the Internet. It is important to make sure that the software you are downloading is coming from a reliable source.
- Java is a prime example of a program that can cause an infection if it is not downloaded correctly. If you are in an Internet browser and a message appears prompting you to update Java from within the browser, then it is likely an unreliable download. If a new version of Java is ready to be upgraded, then your computer will prompt you from the desktop, not from the browser.
Opening Unexpected Emails
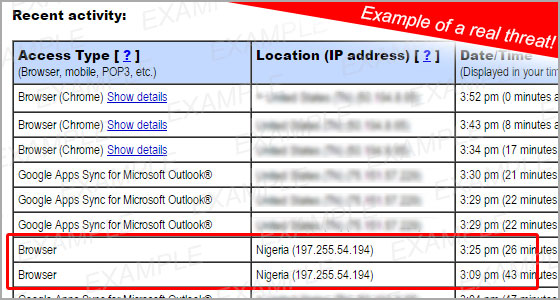
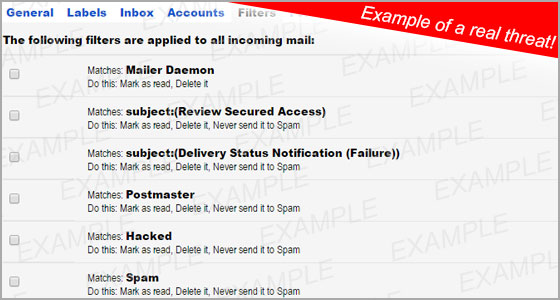
Unexpected emails are yet another way that your computer can contract an infection. Use caution when downloading attachments or opening links from emails as they may contain malware. Strange emails that prompt users to input log-in information are another problem. While you are not necessarily downloading a virus by entering your information, you may be unknowingly giving someone access to your personal information.
Pirating
The unlawful exchange of copyrighted movies, software, or music is not only illegal, but it is also a very easy way to get your computer infected. Many of the files and programs that are available for download on these torrenting sites also include additional files that could contain malware that could lead to an infection in your computer.
Using Antivirus Software and Keeping it Updated
The most effective way to prevent your computer from getting infected is to ensure that it has a reliable Antivirus Software program installed and that it is up to date. Utilising this software keeps your computer running well and it provides protection against any potential malware or other malicious software. Microsoft Security Essentials and Windows Defender are two of the best antivirus software programs on the market today for your PC.
Microsoft Security Essentials covers computers using older Windows operating systems like Windows 7 and Windows Vista. It will provide routine system scanning and cleaning both on and offline. It also provides real-time protection against spyware, viruses, rootkits, and other malicious software.
Windows Defender does much of the same thing that Microsoft Security Essentials does, but it covers newer Windows operating systems such as Windows 8, Windows RT, and Windows 10.
No computer user wants to have to deal with a computer that has been infected with malware, but now that we know more about how computers can get infected, it should be much easier to prevent that from happening. As long as you are cautious and have a good antivirus software program installed, your computer should be protected. If any issues arise with your computer regarding a malware infection, feel free to give us a call at 615-595-6399 or email us at support@tech-pros.com.